Two Factor Authentication (2FA) - What it is and How to Set it Up
A day never goes by that you are unconcerned about your security on the internet. The one method you know to keep your information safe on the net is to regularly change your password. However, passwords on their own do not provide you with enough security as they are now easily picked up by scammers using phishing or brute force. With the continued report of millions of stolen user data every year, you should now realize that passwords alone are not enough to protect your data. What you need is two-factor authentication, sometimes called 2FA or two-step verification or authentication.
This new level of security, however, is not properly understood by the average user like you. So, why don’t you take a seat and let’s go into a simple but detailed breakdown of what 2FA is? Let’s take it from the top.
What are authentication factors?

There are more than a few ways through which you can be authenticated by making use of more than a single authentication method. At this moment, authentication methods rely mostly on knowledge factors and an additional factor for the two-factor authentication methods. Below are some of the authentication factors in use:
- Knowledge factor - it is something known by the user. It could be a password, PIN (personal identification number), or shared data.
- Possession factor - it is mostly something owned by the user, a cell phone, a mobile device/smartphone app, a security token, or an ID card. It is used to approve authentication requests.
- Inherence factor - it is also called a biometric factor. It is usually something personal to the user, an example is fingerprints, facial recognition, voice recognition. Behavioral metrics, such as speech patterns, keystroke dynamics, and gait, are also inherence factors.
- Location factor - it is simply explained by its name. This factor is dependent on the location where an authentication attempt is being executed. Authentication using this factor uses limitations to particular locations, specific devices, tracking of authentication attempt source using IP address and/or GPS.
- Time factor - authentication with this factor restricts the user to a specific time window. Outside of this window, no user is granted access to the system.
Two-factor authentication methods use the first three authentication factors, while systems needing greater security implement multi-factor authentication, using more than two independent factors for secure authentication.
What is Multi-Factor Authentication?

As much as two-factor authentication will provide you with extra security which would make it difficult for attackers to access a system meant for you, sometimes, they manage to get this access. For systems that require higher security, a multi-factor authentication method would be suitable to provide extra security.
A multi-factor authentication method (MFA) can include a three-factor authentication method (3FA) or more. You will usually need a possession factor, knowledge factor, inherence factor, and location factor.
What is Two-factor Authentication?

Two-factor authentication, also known as 2FA is a type of multi-factor authentication. Users confirm their identities and gain access to a system when two different authentication factors are combined. For example, when you use the ATM, you need to have your card, a possession factor, and your PIN, a knowledge factor before you can make a withdrawal. Most systems that use the two-factor authentication always have the knowledge factor (PIN or Password) as the first step of authentication. A second factor can be the possessive, inherence, or location factor.
Why do you need 2FA?
If nothing else, you must have thought, “why all the fuss about an extra layer of protection? I have strong passwords for all my accounts. I don’t need any additional security for my accounts.” In some way, you’re correct to say you have strong passwords for your accounts, however, recently, there’s been a spike in the number of websites that lose their users’ data. Companies who are stagnant and keep using their outdated security systems cannot stand the modern threats and attacks being perpetrated by hackers. While the effect of cybercrime on business, websites, non-profits, and the likes can be staggering, users also suffer from these attacks. Credentials stolen during these attacks are used to obtain fake credit cards that damage the victim’s credit rating. According to a study in 2016, more than $16 billion was stolen from over $15 million U.S. consumers, and in the last six years, over $105 billion have been stolen by identity thieves. This proves to you that websites and businesses need to offer better security to their users.
On the part of the users, they have gradually made passwords a less reliable authentication method. True, having a password is better than not having any protection, however, passwords are not foolproof.
- Bad memory: a report of the study of 1.4 billion stolen passwords showed that a large percentage of them were too simple, having passwords like “123456”, “111111”, “123456789”, “password”, and “qwerty” being the most popular ones. True, it is easy to remember these passwords, but it also wouldn’t take a decent hacker all day to crack these kinds of passwords.
- Fatigue: while some users continuously create weak passwords, some users understand why a complex password is best to protect their accounts. However, over time, these consumers become less motivated when they keep seeing how user information is easily leaked on the dark web. They end up settling for weaker passwords.
- Multiple Accounts: with almost everything being available online, you are required to create more accounts online. With every new account, you create, you are expected to have a new complex password. But, is this possible in any way? Having to create too many passwords soon opens you to the idea of “password recycling”. Hackers are very happy the moment you do this, why? Only a few seconds of testing stolen sign-in credentials, and they will have access to one of your accounts. Once they’ve achieved this, they only need to try the same credentials on other accounts you may own. If you have fallen into the habit of password recycling, which you almost definitely have, then the hackers can access those accounts as well.
Now that you’ve seen how vulnerable you are to hackers when you solely rely on passwords to protect your accounts, then you know having two-factor authentication to provide more security to your account is the least you can do. Let’s say your password is somehow stolen, if you have set up 2FA for your account, a hacker will still need access to your second-factor information before they can get into your account.
Types of 2FA
There are several two-factor authentications in use today, although they are stronger and complex than each other, they all provide better protection than just passwords.
SMS and Voice-based Two-factor authentication

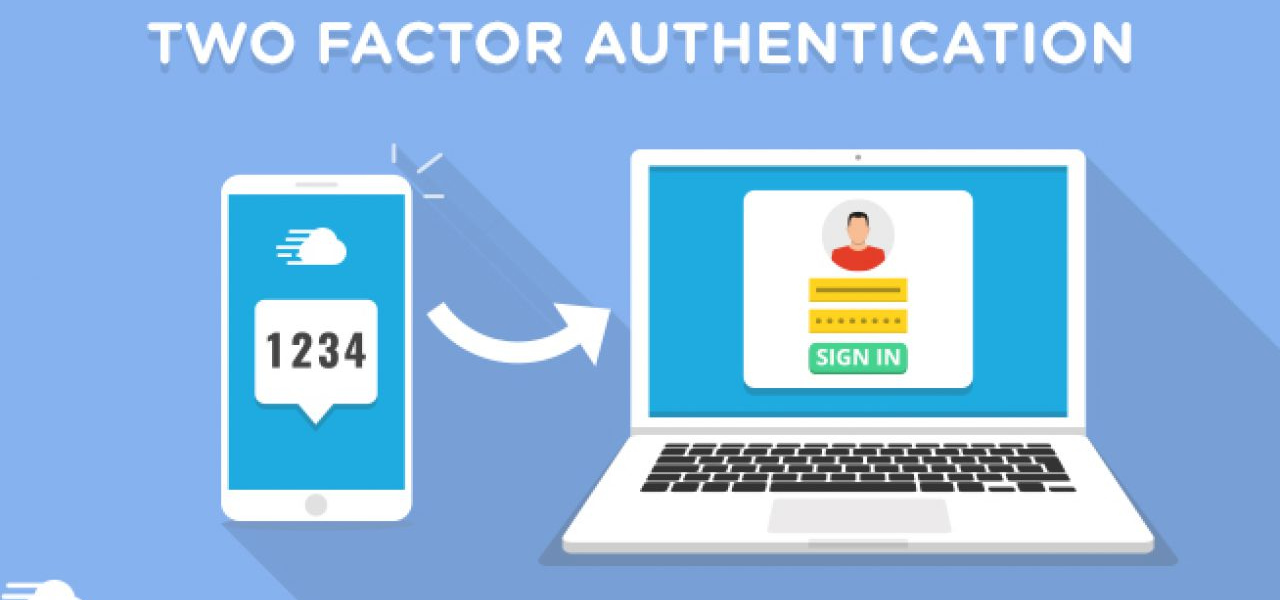
Most times, two-factor authentication involves your mobile phone, which is a suitable alternative to carrying another physical device only for the sake of authentication. You can use your code to access your device, then a one-time-password (OTP) is sent to your phone. It typically consists of 4 to 6 digits sent to you as an SMS. Similar to SMS, voice-based 2FA dials you and dictates your OTP.
By 2018, SMS became the most-used multi-factor authentication method for consumer accounts. However, security experts have criticized the use of SMS and voice-based 2FA as an insecure mode of MFA as it can be easily manipulated using wiretapping or SIM cloning.
So, for your accounts and websites that contain your personal information, you shouldn’t depend on SMS or voice-based 2FA for maximum security.
Hardware tokens

They are usually a small, key fob-like device, and probably the oldest form of 2FA. Hardware tokens can either be connected or disconnected. Disconnected hardware tokens generate a new numeric code every 30-seconds and display it on a built-in screen. You are expected to enter this code when you want to gain access to your account. Connected hardware tokens, however, only require that you plug the token into the computer you will be using. The code is automatically transferred to the system.
While this method of multi-factor authentication is more secure, it is not fully safe from being hacked. You can also easily misplace it due to its small size. Businesses as well find it expensive to produce these tokens.
Software Tokens

In recent times, software tokens have become the most popular mode to carry out two-factor authentication, and a preferred option to SMS and voice-based 2FA. You need to download and install a 2FA app on your smartphone or PC. When you sign-in to any site that supports this particular type of authentication and you enter your username and password, a soft-token or time-based, one-time passcode (TOTP) is generated and sent to the 2FA app, and you will be prompted to provide it.
Software token has become the most-used form of two-factor authentication because the code is generated and used on the same device, which lessens the possibility of interception by hackers, something of major concern using SMS and voice-based 2FA.
Push Notification

Another option most websites and apps choose is to send their users a push notification informing them of an authentication attempt. This push notification is sent to any device you have registered as secure, and you are expected to either approve or deny this authentication attempt after reviewing the details. You do not need to enter any password, neither are you supposed to provide a code.
Push notification further eliminates the risk of man-in-the-middle attacks, phishing, and unauthorized access. While it is easily the most secure type of 2FA for consumer-based authentication, push notification requires an internet connection and a smartphone that installs apps.
Biometrics
Not readily available to the public, Biometric 2FA considers the user to be the token. Verification of a person’s identity using fingerprints, facial recognition, and retina patterns are already in use for Biometric 2FA. However, keystroke patterns, vocal prints, ambient noise, and pulse are among the forms being studied to be used in the future for multi-factor authentication.
Services with 2FA
Below, we discuss some of the popular services that have 2FA ability in a bid for you to be more secure on as many apps and websites as possible.
Google 2-Step Verification
Google understands that you have almost all of your life on Google, and that is why it began working on a 2FA system in 2010 which it calls 2-Step Verification. If 2-Step Verification is on for your Google account, you can use the Google Prompt. All you need to do is ensure the Google Search app is on your phone, whenever you log in to your Google account on any device, you will be sent a push notification and all you’re required to do is tap to approve the sign-in.
You can as well use the Google Authenticator app to generate a verification code, especially when your smartphone is not connected to the internet. However, you must have previously been signed up for 2-Step Verification to be able to use it. A QR code is generated on your desktop screen which you have to scan. Next, you get a time-based or counter-based code to input.
You are also allowed to select a phone number where you can receive codes or get 10 unused codes that you can scribble somewhere for an emergency. Visit your Google account security settings to get this done.
Facebook Two-factor Authorization
Go to Security and log in under Settings when you log in to Facebook on your desktop. You’ll see the Two-factor Authentication option, click Edit, and choose your second form of authentication. You should choose to use an authenticator app. Facebook will generate a QR code on your desktop screen, and you scan the code using the authenticator app on your smartphone. Whenever you sign-in to Facebook and you are asked for your six-digit code, launch your authenticator app and retrieve the code from there. Just like Google, you can also get a list of 10 recovery codes to use during an emergency and you don’t have your phone with you. Just ensure you keep them in a safe place.
Instagram Two-factor Authentication
Go to your profile, on the top right corner, tap the hamburger menu. Go to Setting > Privacy and Security > Two-factor Authentication, and select where you want your authentication to be sent. You can either turn on Text Message or turn on Authentication App. You will be directed on how to set things up. You are also provided with a list of five recovery codes to be used in the future when you try to login from other devices.
Whatsapp Two-step Verification
Asides from its end-to-end encryption, WhatsApp also has two-step verification to further protect its users from snoops and hacks. Simply go to your Setting, under Account, you can tap Enable to activate Two-step Verification. You are expected to create a six-digit PIN, and provide an email should in case you ever need to turn off verification. Whenever you sign out or log in with a different device to your WhatsApp, you need to re-enter your PIN.
Twitter Login Verification
On your desktop, click your profile photo, click Setting and Privacy from the drop-down list. Click Set up Login verification, next, you’ll enter your Twitter password and to link a phone number to your account if one isn’t linked yet. On your mobile app, tap your profile picture, go to Setting and Privacy, under Security in the Account Menu, you can toggle on or off Login Verification.
You can as well get a list of codes to be used whenever you are in an emergency or cannot access your device.
Apple Two-factor Authentication
For iOS and Mac users, access to your iCloud, iTunes, App Store, Apple Books, and Apple Music can be secured with 2FA. Sign in to your My Apple ID page. Go to Security > Two-factor Authentication, click Get Started. You will be directed on the necessary steps to set up two-factor authentication for your Apple device(s). If you’re using iOS, go to Settings > Your name > Password & Security > Turn on Two-factor Authentication.
To complete your setup, you’ll need to provide answers to two of your three security questions, reconfirm credit card information, and enter a valid phone number. If the phone number is on the same phone, the code will be automatically inputted when you receive it.
Similar to other platforms, you can get a code to login at the moment you need it. On your iOS device, go to iCloud Setting > Tap your Username > enter Apple ID password > Password & Security > Get Verification Code.
Many other platforms offer two-step authentication such as Microsoft Two-step Verification, Amazon Two-step Verification, Yahoo Account Key, Reddit Two-factor Authentication, Slack Two-factor Authentication, Dropbox Two-step Verification, PayPal 2-Step Verification, Wordpress Two-step Authentication, Fortnite Two-factor Authentication amongst many.
Among the leading cause of security breaches are stolen, reused, and weak passwords, and since passwords have remained the main way companies secure their users and their information, it is pertinent to you as a user to avoid saving your important information on apps and websites that do not provide a layer of extra security in terms of 2-Factor Authentication or other forms of Multi-factor Authentication.












Leave a comment
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.